
Problem Statement

Law enforcement agencies face growing challenges from cyber threats, data breaches, and strict regulatory compliance. Protecting sensitive data, securing communications, and ensuring critical systems stay operational require a robust, comprehensive cybersecurity strategy.
Cybersecurity Risks:
Law enforcement systems are prime targets for cyberattacks like ransomware and phishing, risking operational disruption and data compromise.
Data Privacy:
Securing sensitive information such as criminal records and investigation data is crucial to maintaining trust and privacy.
Regulatory Compliance:
Adhering to standards like CJIS is vital to avoid penalties and ensure public confidence in the system.
Operational Continuity:
Maintaining constant availability of critical systems is essential for effective incident response and communication.
Tech Integration:
Adopting technologies like AI, IoT, and body cameras demands enhanced security to mitigate new vulnerabilities.


Compliance standards for law enforcement agencies

Law enforcement agencies must comply with a variety of standards to safeguard sensitive data, secure communications, and meet privacy requirements, with these standards differing across regions and jurisdictions. Some key compliance standards include:

An international standard for information security management, ISO 27001 helps organizations implement best practices for securing sensitive data, including the personal and criminal records managed by law enforcement.

The National Institute of Standards and Technology (NIST) provides a cybersecurity framework often used in the U.S. to help agencies identify, protect, detect, respond, and recover from cyber threats.

Specific to U.S. law enforcement, CJIS(Criminal Justice Information Services Security Policy) provides guidelines for securing criminal justice information, ensuring data protection across local, state, and federal agencies.

This Indian law governs the handling and protection of digital information, including guidelines for securing data and preventing cybercrime, making it relevant for Indian law enforcement agencies.

Digital Personal Data Protection Act (DPDP) Indian law governs how personal data is handled, ensuring that law enforcement agencies comply with data privacy standards while handling and processing personal data.

General Data Protection Regulation applicable to agencies operating in or handling data from the European Union, GDPR mandates strict protocols for processing and protecting personal data, ensuring privacy and security.
These standards help law enforcement agencies maintain compliance, protect sensitive data, and ensure operational resilience across various regions and legal frameworks.
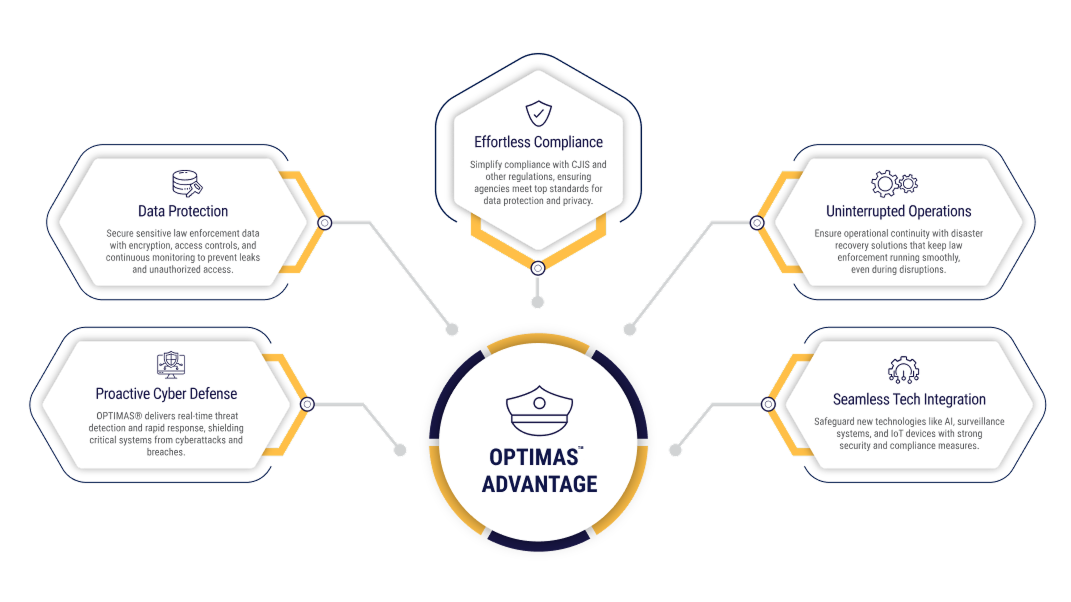
OPTIMAS™ for Law Enforcement
OPTIMAS™ provides law enforcement with tailored cybersecurity solutions to safeguard critical data and ensure operational efficiency.
Asset Management:
Continuously monitor and evaluate the security posture of critical assets, such as databases, surveillance systems, and communication networks, to detect and mitigate vulnerabilities as they arise ensuring operational safety and resilience.
Data Integration for Law Enforcement:
Seamlessly aggregate and correlate data from various systems—such as crime databases, surveillance feeds, and communication networks—using standardized frameworks to enhance situational awareness and decision-making in real time.
Automated Workflow Process Optimization:
Implement continual automation and monitoring of workflow processes to improve efficiency, reduce errors, and enhance overall operational security.
Blind Spot Identification:
Automate discovery to track down unaccounted devices that could be security risks.
Configuration, Vulnerabilities & Threats:
Protect against cyberattacks by addressing misconfigurations and unauthorized access.
Continual Insights and Posture Management:
Enhance reporting and quality of security posture with increased frequency.
Autonomous Compliance Library:
Leverage an automated compliance library to continuously update and enforce security controls and policies (such as CJIS, NIST, and IT Act), to ensuring adherence to regulatory standards and best practices.
Adaptive Control Orchestration and Validation:
Implement continual adaptive orchestration and validation of security controls to dynamically adjust and verify their effectiveness in response to changing threats and system configurations.
Privacy Compliance Monitoring:
Continuously oversee and enforce privacy policies and controls to ensure that sensitive data is protected, and regulatory requirements are met.
Configuration Compliance:
Enhance reporting and quality of security posture with increased frequency.
Protect Your Law Enforcement Systems Now
Secure, compliant, and resilient—ensure your agency's systems are prepared for any threat. REQUEST A DEMO today to see how OPTIMAS™ strengthens your cybersecurity and operational capabilities while ensuring full regulatory compliance.
