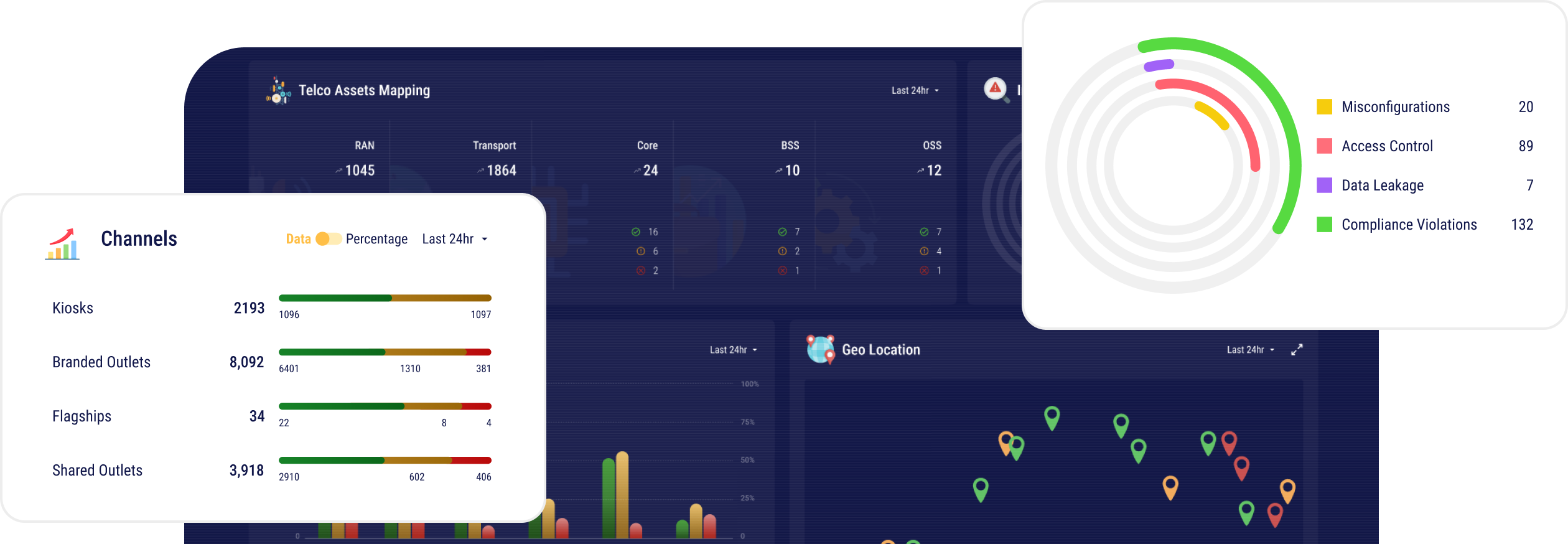
Problem Statement

OEM-specific & complex telecom networks with multiple vendors and suppliers make it unmanageable for CISOs to keep up with all telecom security aspects and technical standards, leading to possible security blind spots and attacks.
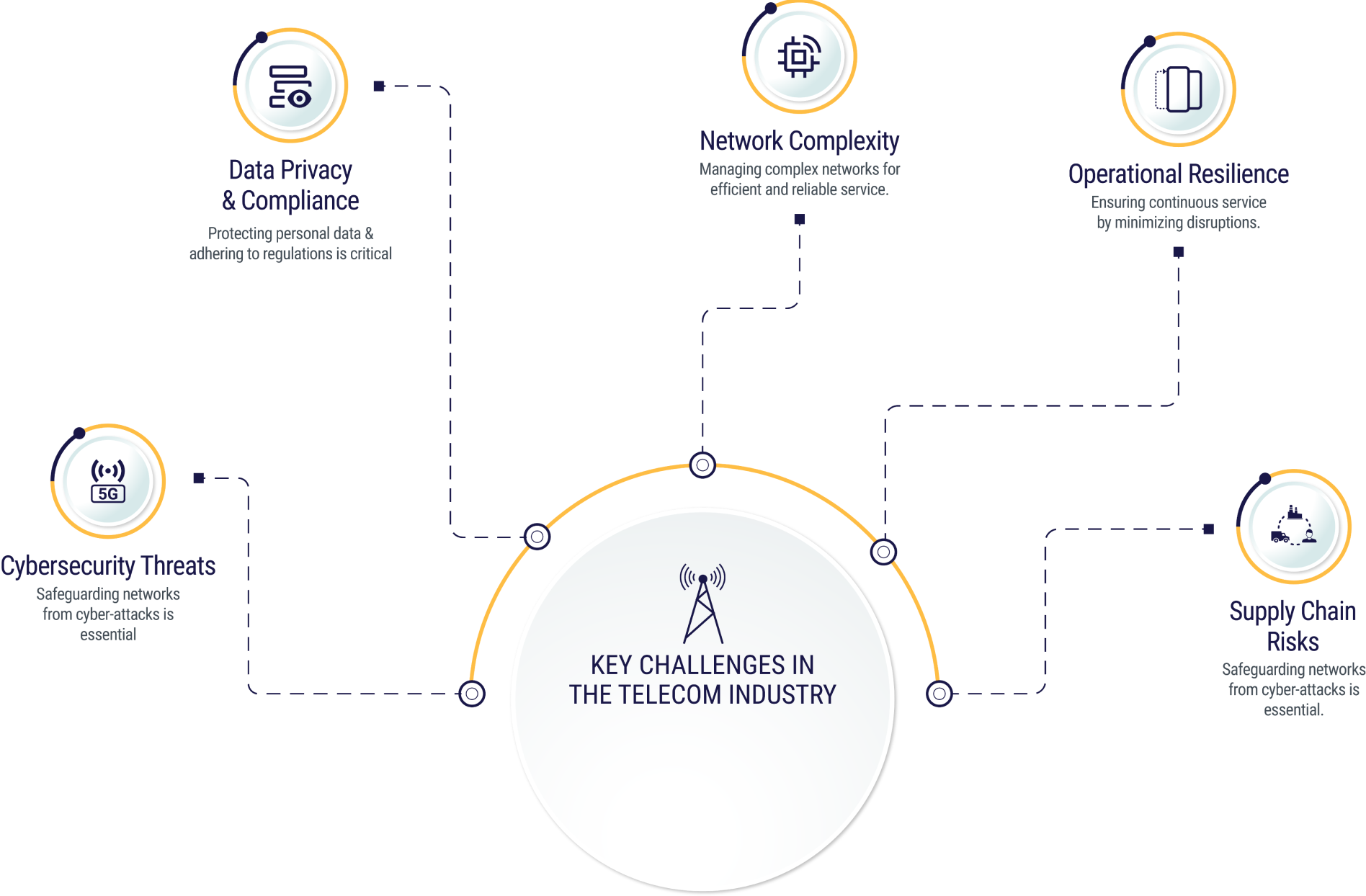


Cybersecurity Threats:
Telecom networks are prime targets for cyberattacks like DDoS, malware, and insider threats. The complexity of these networks makes them hard to protect against evolving dangers.


Data Privacy and Compliance :
Handling vast amounts of customer data, telecom operators must comply with regulations like CIS CSC, NIST CSF, PCI-DSS, ISO2701, and other regional regulations. Non-compliance can lead to hefty fines and reputational damage.


Network Complexity :
Integrating technologies like 5G, IoT, and edge computing adds layers of complexity, making seamless security and interoperability a significant challenge.


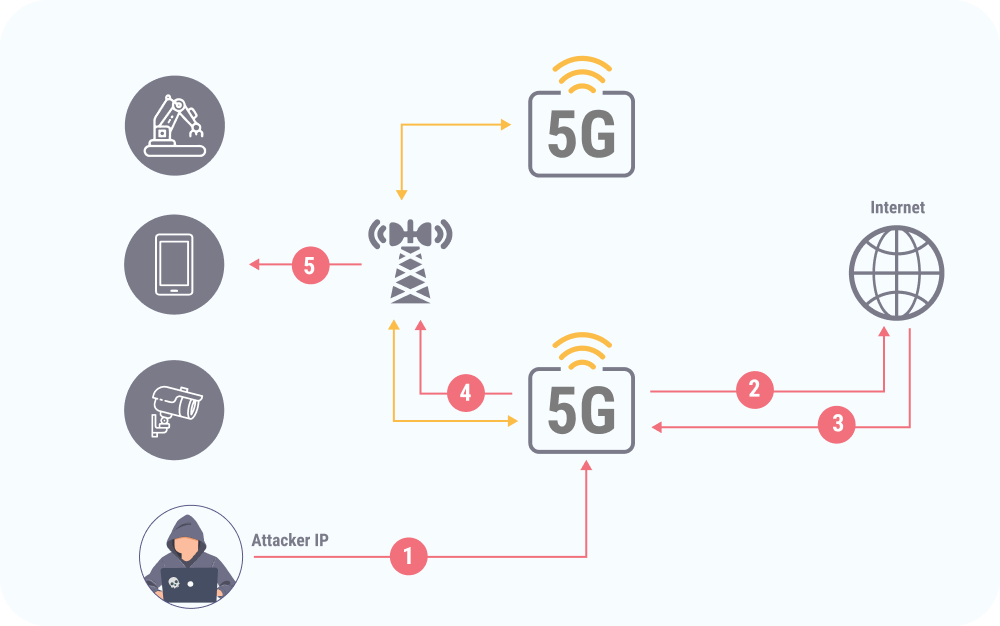
Operational Resilience :
Telecom services are vital to society. Disruptions from cyberattacks, natural disasters, or system failures can have far-reaching impacts, making continuous service delivery essential.


Supply Chain Risks :
Relying on a global supply chain exposes telecom networks to vulnerabilities in third-party vendors, making hardware and software security critical.

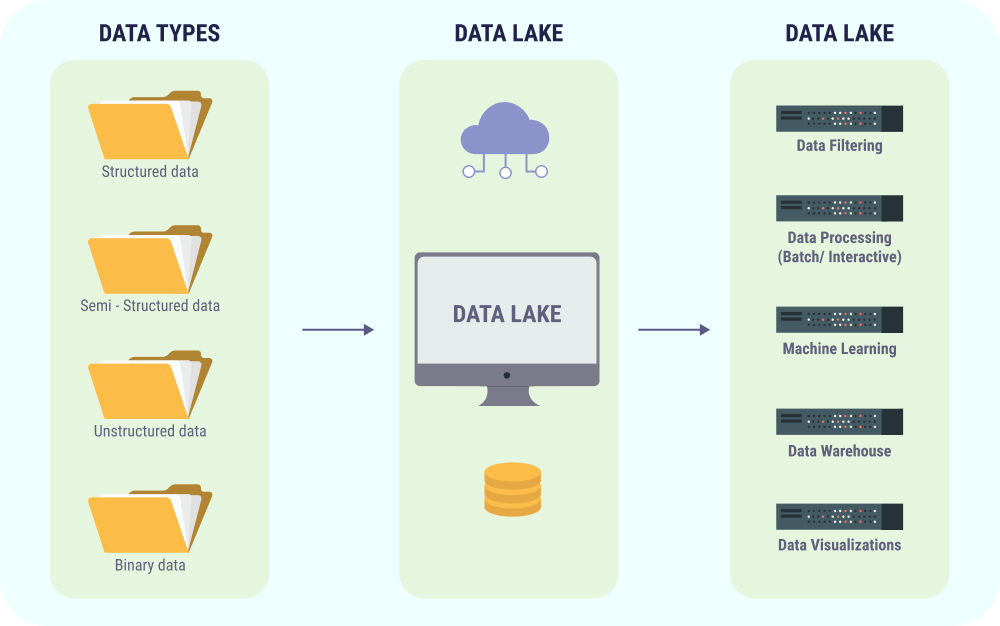

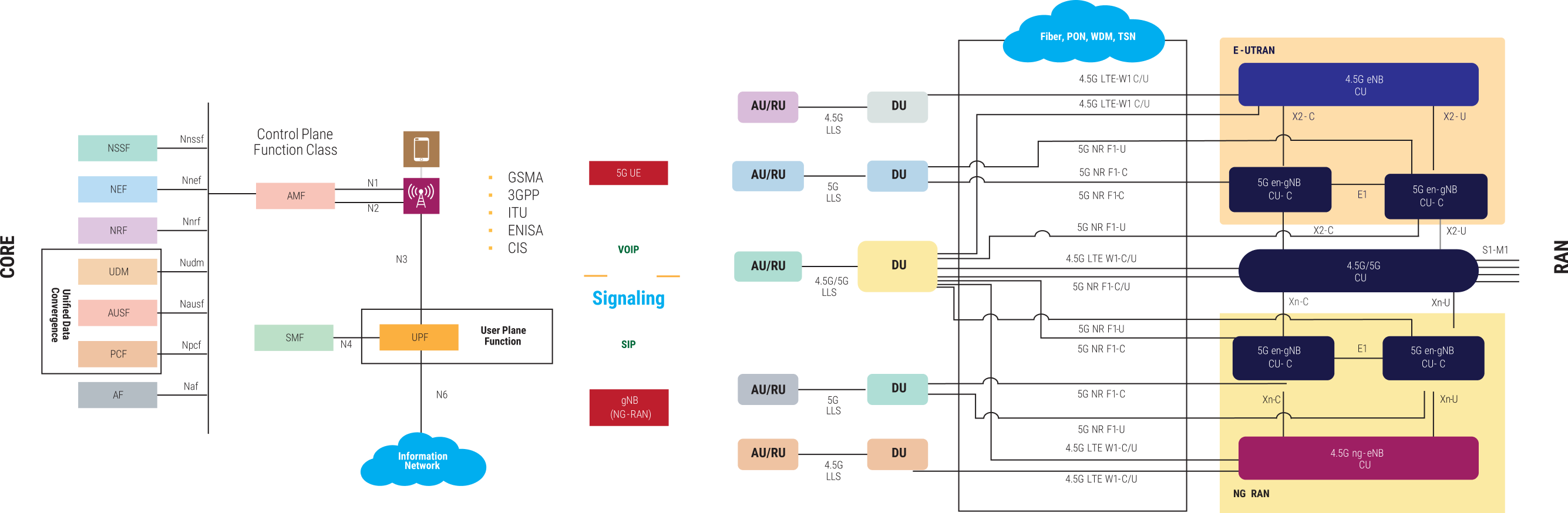
Key trends influencing telecom security :

Transition from closed proprietary communication to open standards network.

Shift from proprietary protocols/hardware/IoS to generic IT hardware and IP-based protocols.

Increase in the involvement of IT companies as OEMs

Convergence of telecom networks with enterprise IT systems.

Regulatory audits becoming important to ensure security assurance.
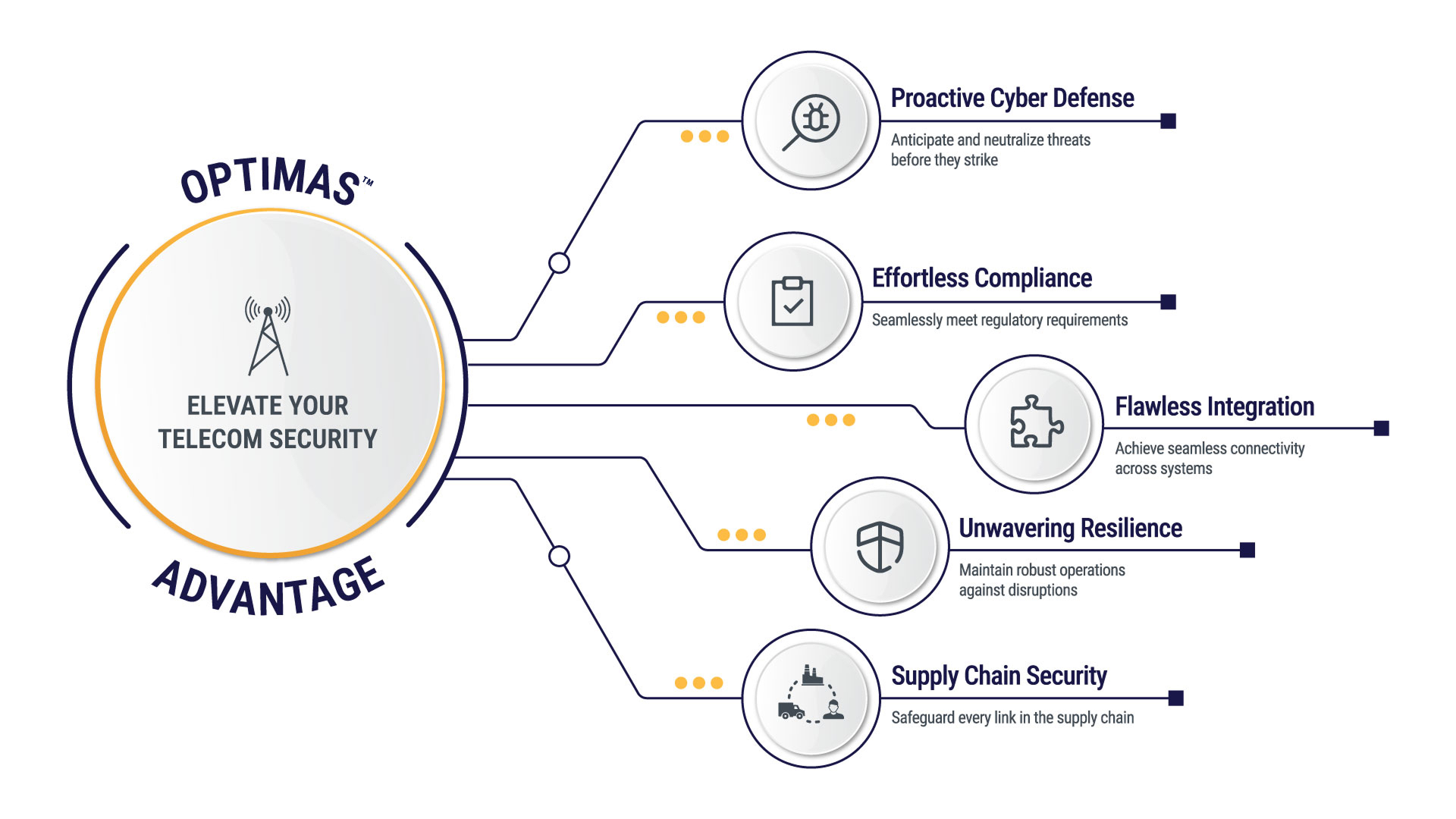
OPTIMAS™ Advantage: Elevate your Telecom Security


Proactive Cyber Defense :
OPTIMAS™ brings advanced threat detection and response, continuously monitoring your network to spot vulnerabilities and stop breaches before they happen.

Effortless Compliance :
Say goodbye to compliance headaches. OPTIMAS™ automates checks and provides continual audit trails, ensuring you stay aligned with CIS CSC, NIST CSF, PCI-DSS, ISO2701, and other regional regulations.

Flawless Integration :
Seamlessly integrate cutting-edge 5G and IoT technologies with OPTIMAS™™, ensuring smooth, secure interoperability across your network.
Unwavering Resilience :
With OPTIMAS™, your network is always prepared. Our robust disaster recovery plan guarantees uninterrupted service, even during cyberattacks or natural disasters.
OPTIMAS™: Empowering Secure and Resilient Telecoms

Comprehensive Network Security
OPTIMAS™ delivers a robust network security framework designed to protect telecom networks from a wide range of cyber threats. By continuously monitoring network traffic, detecting anomalies, and mitigating risks in continual, OPTIMAS™ ensures the integrity and reliability of telecom services.

Fraud Detection & Prevention
OPTIMAS™ equips telecom providers with advanced tools to detect and prevent fraud. Leveraging AI and machine learning, our platform analyzes vast amounts of data to identify suspicious activities and prevent fraudulent transactions before they occur.

Compliance & Risk Management
OPTIMAS™ simplifies the complex regulatory landscape for telecom providers by automating compliance checks and offering continual visibility into compliance status. Our platform ensures that operators meet regulatory requirements while minimizing the risk of non-compliance..

Operational Continuity and Resilience
OPTIMAS™ guarantees that telecom networks remain resilient and operational even in the face of cyberattacks, natural disasters, or system failures. Our platform supports disaster recovery planning and continual threat detection to ensure continuous service delivery.

Supply Chain Security
OPTIMAS™ strengthens telecom supply chain security by monitoring and assessing third-party vendors for potential vulnerabilities. Our platform helps safeguard hardware and software integrity, reducing risks associated with global supply chain dependencies.

Seamless Integration and Interoperability
OPTIMAS™ ensures smooth integration of 5G, IoT, and other advanced technologies across telecom networks. Our platform supports secure, seamless interoperability, reducing complexity and enhancing the efficiency of your technology infrastructure.
Ready to Secure Your Energy Infrastructure?
Shield your systems from breaches and attacks. Request a demo to discover how OPTIMAS™ fortifies your network, ensures compliance, and maintains operational excellence.