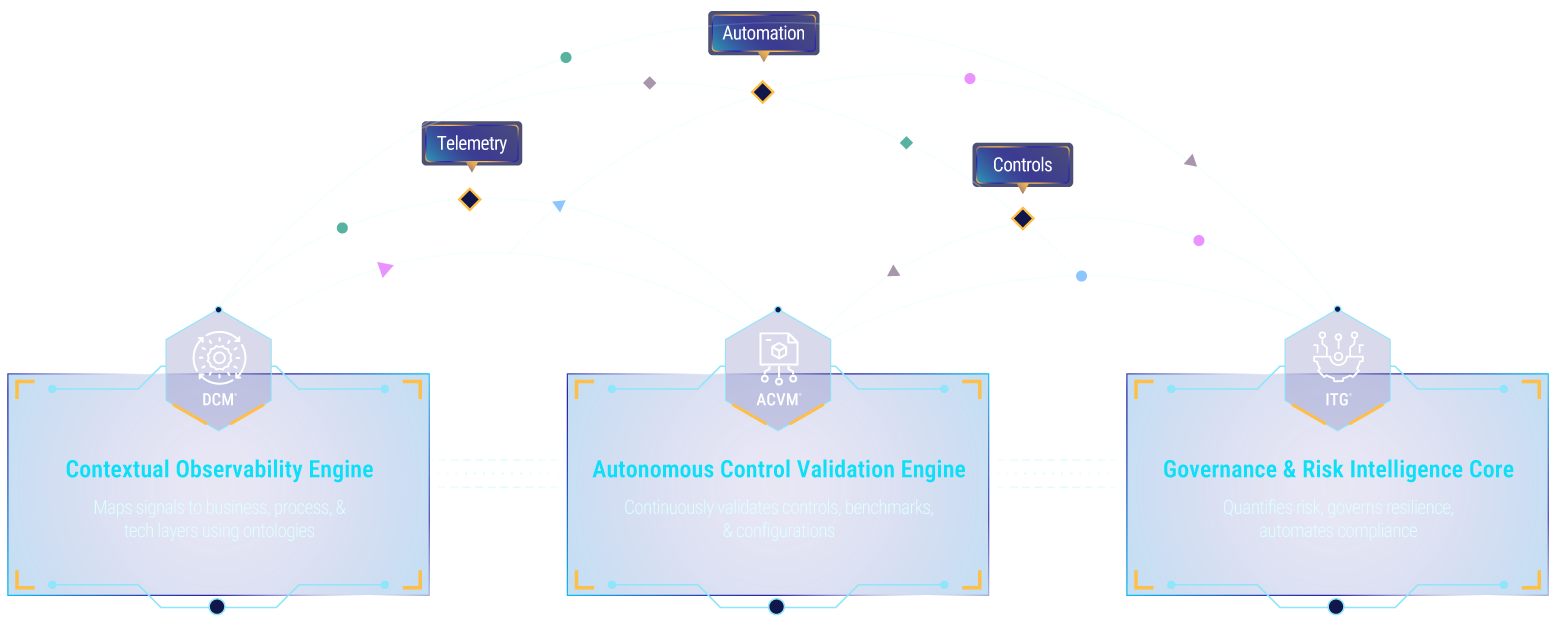
Your Trust Quantification Engine - Powered by Three Intelligence Layers
OPTIMAS™ is your Trust Quantification Engine. It continuously ingests your compliance, security, risk and resilience telemetry, maps it against your unique business context, and autonomously computes a real-time Trust Score, so you can anticipate threats, validate controls, govern outcomes, and act on trust signals across the enterprise.
Under the hood are three modular intelligence layers that feed your Trust Score:
-
DCM™ (Digital Context Management)
For continual observability
-
ACVM™ (Autonomous Control Validation & Monitoring)
For continual compliance
-
Integrated GRACE™ (Governance, Risk, Assurance, Compliance & Exposure)
For unified risk & resilience Governance